Computer System Security Introduction: Introduction, What is computer security and what to l earn? , Sample Attacks, The Marketplace for vulnerabilities, Error 404 Hacking digital India part 1 chase
Web security landscape : Web security definitions goals and threat models , HTTP content rendering .Browser isolation .Security interface , Cookies frames and frame busting, Major web server threats ,Cross site request forgery ,Cross site scripting ,Defenses and protections against XSS , Finding vulnerabilities ,Secure development
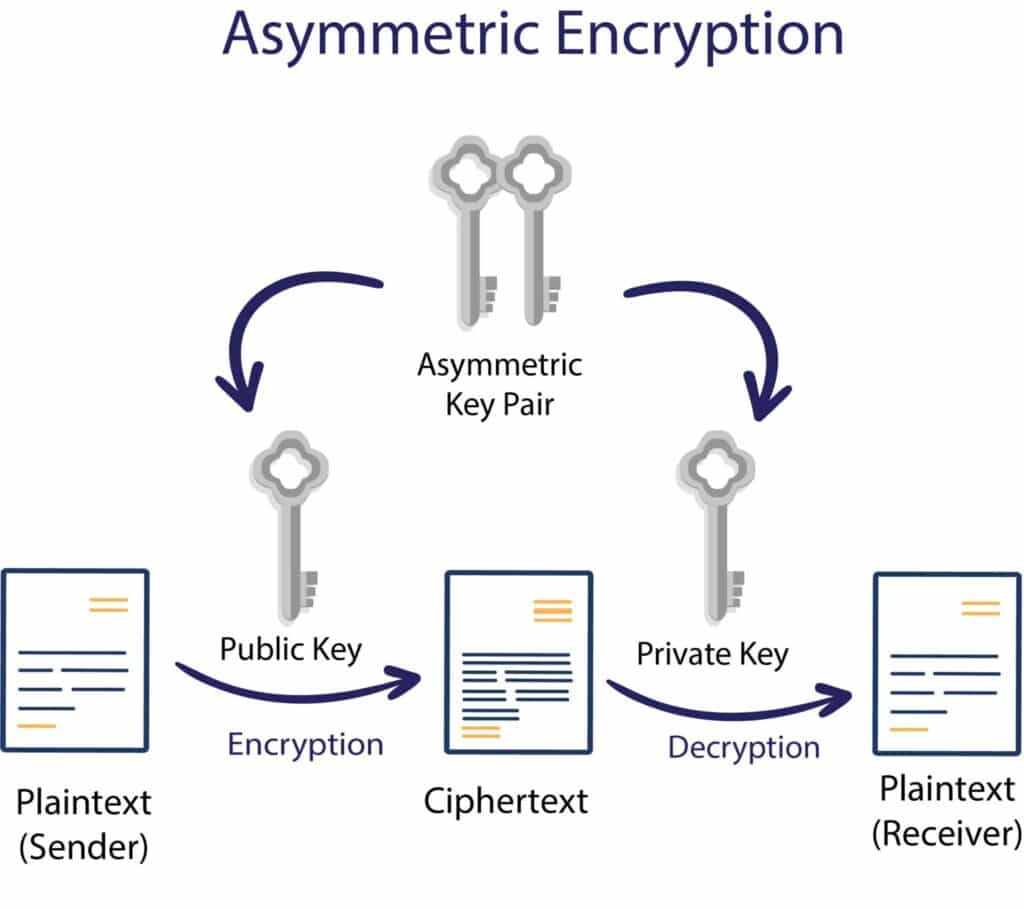
Basic cryptography: Public key cryptography ,RSA public key crypto ,Digital signature Hash functions ,Public key distribution ,Real world protocols ,Basic terminologies ,Email security certificates ,Transport Layer security TLS ,IP security , DNS security
Internet Infrastructure: Basic security problems , Routing security ,DNS revisited ,Summary of weaknesses of internet security ,.Link layer connectivity and TCP IP connectivity , Packet filtering firewall ,Intrusion detection.
Ans. :Computer security is an essential aspect of information technology that ensures the confidentiality, integrity, and availability of computer systems and their data. With the increasing reliance on computers and the internet in our daily lives, the need for effective security measures has become more important than ever. In this context, understanding the common types of attacks on computer systems and how to prevent them is crucial.
The ultimate goal of information security is to maintain the CIA triad within an organization. The elements of the CIA triad are:
Confidentiality: This means ensuring that only the authorized users have access to information. Whenever a company suffers from a data breach or data leak and individuals’ information is accessed by criminals, the public or employee’s that don’t have the proper authorization, confidentiality has been compromised. Some of the key security controls that you can use to maintain confidentiality are:
Encription : Encrypting information ensures that even if an unauthorized user is able to get access to the information, without the decryption key the information will be in an unreadable format and therefore confidentiality will be maintained.
Strong Passwords : By having strong passwords it reduces the chances of someone being able to access accounts or resources by guessing the password.
Two factor authentication: 2FA supplements traditional login information (username and password) by requiring an additional code before granting someone access to a resource.
Identity Access Management : IAM is the practice of ensuring that only the correct individuals are given access to resources. It follows something called the “least privilege model”, this means that users should only be given access to the resources needed to do their job and nothing more. This helps to enforce the confidentiality of information.
Proper Technical Controls: Technical controls include things like firewalls and security groups. These controls prevent people from accessing the company’s network and prevents them from obtaining company information without authorization.
Physical Locks and Doors: Physical security measures like cabinet locks, vaults, biometric scanners and door locks prevents people from physically sneaking into the company and taking company documents.
Integrity: To protect information from being modified by unauthorized people and ensures that the information is trustworthy and accurate. Anytime information is modified by someone that isn’t authorized to do so, whether it was someone inside the company or outside, it is a violation of the information’s integrity. An example would be if the CFO sends a document to be examined or reviewed by the director of finance. The director of finance may try to manipulate the information without the CFO knowing in order to make his/her department look better, launder money etc. You need to have a means of knowing whether or not a document has been modified without your knowledge so that you can trust that document’s integrity. Also, in the event data is lost, you need to be able to recover all of that data or at least most of it from a trusted source. Some controls you can use to maintain integrity are:
Hashes: A hash is the output of a hashing algorithm such as MD5 or SHA. A hash algorithm takes a message of any size and creates a fixed sized value called a hash (eg 12 characters long). If any character in the original message is changed, it will result in a different hash being generated. By creating a hash of a message when you first receive it, you can later test to see if that message has been altered in any way.
For example, say I have a word document on March 10th 2020, I use a hash algorithm to generate the hash 123456789. Then on March 15th, I want to check if anyone has modified that file, I can use the hash algorithm again and if the hash created is not the same, I know someone changed the contents of that file.
Secure Backups: By creating secure backups if you ever have doubts about the integrity of the data on a system you can reboot that system using the information you have in your backups. Hashes can be used with your backups to ensure that they have not been altered in any way. This way you can be confident that the information you are using to reboot your systems is accurate. A good example of when you will need this is if your company ever suffers a ransomware attack and is unable to recover your data.
User access controls: By controlling what information users have edit access to, you limit the potential for users to edit information without permission.
Availability: To ensure that the information is accessible to authorized people whenever it is needed. An example of this would be a website like Netflix. For most companies they want availability of at least 99.99%, which means that 99.99% of the time you go to Netflix you should be able to access the services that you want. In order to do this there are several practices you can implement to ensure that your company will have a high uptime:
Off site backups: Having off site backups ensures that if something happens you have a copy of data to restart your systems and keep your business going.
Disaster Recovery: These plans outline how your company should respond to certain types of situations such as earthquakes, floods, fires, hurricanes etc
Redundancy: This is when you make multiple instances of network devices and lines of communication so that if one device or line fails it doesn’t cause a loss of availability.
Failover: This is a backup node (system) that automatically switches into production in the event that the primary system fails.
Virtualization: This is the process of creating a software (virtual) version of something that physically exists. Usually this takes one piece of hardware and enables it to run multiple operating systems in virtual machines (VMs), this way you can have redundancy even though you only have 1 physical machine.
Proper Monitoring of the environment: You want to have proper monitoring through tools like a SIEM. This way you will know as soon as there is a problem in your environment and you can address the issue asap.
types of cyber attacks
Domain Name Server (DNS) spoofing is a cyber attack that alters DNS to redirect online traffic to a fake website that emulates a legitimate one. In this type of cyber attack, the victim introduces their username and password to log in, thus giving this data to hackers.
Cross-site scripting
Rootkits
Rootkits refer to a group of software tools that allow criminals to get unauthorized access to a system without being detected. A rootkit hides malicious programs that reach into devices through spam or other ways. When the rootkit is activated, a backdoor is set up, and criminals might install other forms of malware such as ransomware or trojans.
DoS and DDoS attacks
A Denial of Service (DoS) attack is meant to crash a network by flooding it with traffic. The site receives many requests, and the resources get overwhelmed. Consequently, the website cannot respond, shutdowns and becomes inaccessible to users.
A Distributed Denial of Service (DDoS) attack is a DoS attack that uses multiple machines to flood the targeted network. This attack employs various remote devices, bots, or zombies, allowing the attacker to send vast amounts of traffic from different locations simultaneously. The server is overloaded more rapidly than in a regular DoS attack.
Malware
The first type of cyber attack is one that you're surely familiar with. Malware is a broad term that includes different types of malicious software, including viruses, worms, and spyware. Malware attacks exploit a vulnerability and break into the network to plant the malicious code.
How to prevent cyber attacks
1. Use complex passwords
Passwords should be eight characters long and combine numbers, letters, symbols, and cases. You shouldn't use the same passwords in all your accounts; they should be changed every time. Since remembering so many different passwords could be a real mess, you could resort to password generators.
2. Enable multi-factor authentication
Passwords are only the first layer of protection and can be easily attacked and deciphered. You should also enable multi-factor authentication on all your accounts with an authenticator app or a physical security key. Using SMS is not recommended because attackers might intercept this information.
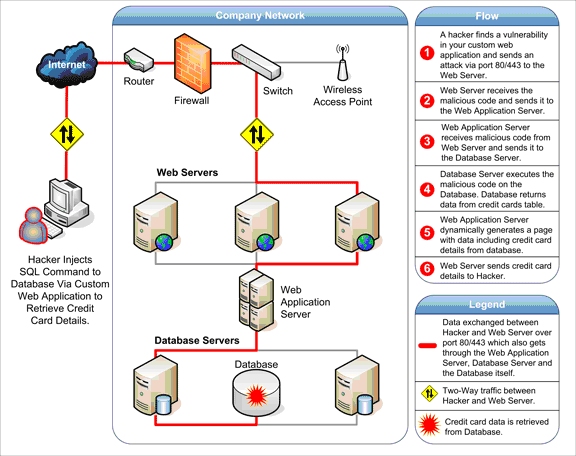
Ans. A control hijack attack is done by overwriting some of the data structures in a victim program that affects its control flow and eventually hijacks the control of the program and possibly the underlying system. Attacks like these eventually pave way for corrupting or overwriting the data that they were storing.
Control Hijacking Download
What is the confinement principle, and how can it be used to enhance security?Ans. The confinement principle is another important aspect of computer security. It involves limiting the actions that a user or program can perform to prevent unintended consequences. This principle is implemented using confinement techniques, such as VM-based isolation and software fault isolation, to enhance security.
Confinement Principle : Download
The Three Main Types of Access Control
1. Role-Based Access Control (RBAC)
RBAC is the most traditionally well-known and popular type of access control. The RBAC model allows owners to assign access to the network based on defined user profiles. These profiles are based on their roles, such as managers, temporary contractors, and heads of departments.
2. Attribute-Based Access Control (ABAC)
ABAC stems from RBAC but provides access control on a more granular level. The ABAC model allows application or line managers to use attributes, or characteristics about the access request, entitlement, or user. These attributes can be based on desired outcomes for what an identity will do with said access, what the resource or system being requested is, the location of the request, and more.
3. Policy-Based Access Control (PBAC)
PBAC evaluates access rights and entitlements that can be adjusted based on new corporate policies. As organizations change, they often will write new policies to ensure that access rights are consistent, appropriate, and secure. While PBAC and ABAC are very similar, but the key difference is that policies inform the IGA solution what to do and how to enforce access, and attributes look reactively to the IGA solution and inform the engine how to provide access.
Rootkits
Rootkits refer to a group of software tools that allow criminals to get unauthorized access to a system without being detected. A rootkit hides malicious programs that reach into devices through spam or other ways. When the rootkit is activated, a backdoor is set up, and criminals might install other forms of malware such as ransomware or trojans.
DoS and DDoS attacks
A Denial of Service (DoS) attack is meant to crash a network by flooding it with traffic. The site receives many requests, and the resources get overwhelmed. Consequently, the website cannot respond, shutdowns and becomes inaccessible to users.
A Distributed Denial of Service (DDoS) attack is a DoS attack that uses multiple machines to flood the targeted network. This attack employs various remote devices, bots, or zombies, allowing the attacker to send vast amounts of traffic from different locations simultaneously. The server is overloaded more rapidly than in a regular DoS attack.
Malware
The first type of cyber attack is one that you're surely familiar with. Malware is a broad term that includes different types of malicious software, including viruses, worms, and spyware. Malware attacks exploit a vulnerability and break into the network to plant the malicious code.
It ensures the integrity of your data
Cryptography protects the confidentiality of information
It assures that the sender or receiver is the right one
Ransomware Attack
The goal of a ransomware attack is to gain exclusive control of critical data. The hacker encrypts and holds your data hostage and then demands a ransom payment in exchange for the decryption key you need to access the files. The attacker may even download and threaten to release sensitive data publicly if you do not pay by a deadline. Ransomware is the type of attack you’re most likely to see reported in major news media.
Code Injection (Remote Code Execution)
To attempt a code injection, an attacker will search for places your application accepts user input – such as a contact form, data-entry field, or search box. Then, through experimentation, the hacker learns what various requests and field content will do.
Cross-Site Scripting (XSS) Attack
JavaScript and other browser-side scripting methods are commonly used to dynamically update page content with external information such as a social media feed, current market information, or revenue-generating advertisements.
Malware and Virus Infection
Malware is short for malicious software. Malware on a workstation can encrypt data for ransomware purposes or even log keystrokes to capture passwords. Hackers typically use malware to expand existing access to your site or spread access to others on the same network.
Packet Filter Firewall and Application Level Gateway
- It works in the network layer of the OSI Model. It applies a set of rules (based on the contents of IP and transport header fields) on each packet and based on the outcome, decides to either forward or discard the packet.
- Packet filter firewall controls access to packets on the basis of packet source and destination address or specific transport protocol type. It is done at the OSI (Open Systems Interconnection) data link, network, and transport layers. Packet filter firewall works on the network layer of the OSI model.
- Packet filters consider only the most basic attributes of each packet, and they don’t need to remember anything about the traffic since each packet is examined in isolation. For this reason, they can decide packet flow very quickly.
- Example: Filter can be set to block all UDP segments and all Telnet connections. This type of configuration prevents outsiders from logging onto internal hosts using Telnet and insider from logging onto external hosts using Telnet connections.
Difference :
| Packet filter | Application-level |
|---|---|
| Simplest | Even more complex |
| Screens based on connection rules | Screens based on behaviour or proxies |
| Auditing is difficult | Activity can audit |
| Low impact on network performance | High impact on network performance |
| Network topology can not hide | Network topology can hide from the attacker |
| Transparent to user | Not transparent to the user |
| See only addresses and service protocol type | Sees full data portion of a packet |








Comments